Overview
This guide will show you how to create a GCP Workload Identity Federation Provider, and attach it to a Service Account to generate temporary credentials by accepting env zero’s OIDC token. Refer to env zero’s OIDC configuration.Workload Identity Federation Pool and Provider
- Login to your GCP account and select the relevant project.
- In the left-hand side menu select
IAM & Admin - Go to
Workload Identity Federationpage - Click on the
Create Poolbutton - Enter a name and description, make sure the
Enabled Poolis selected and click on theContinuebutton.
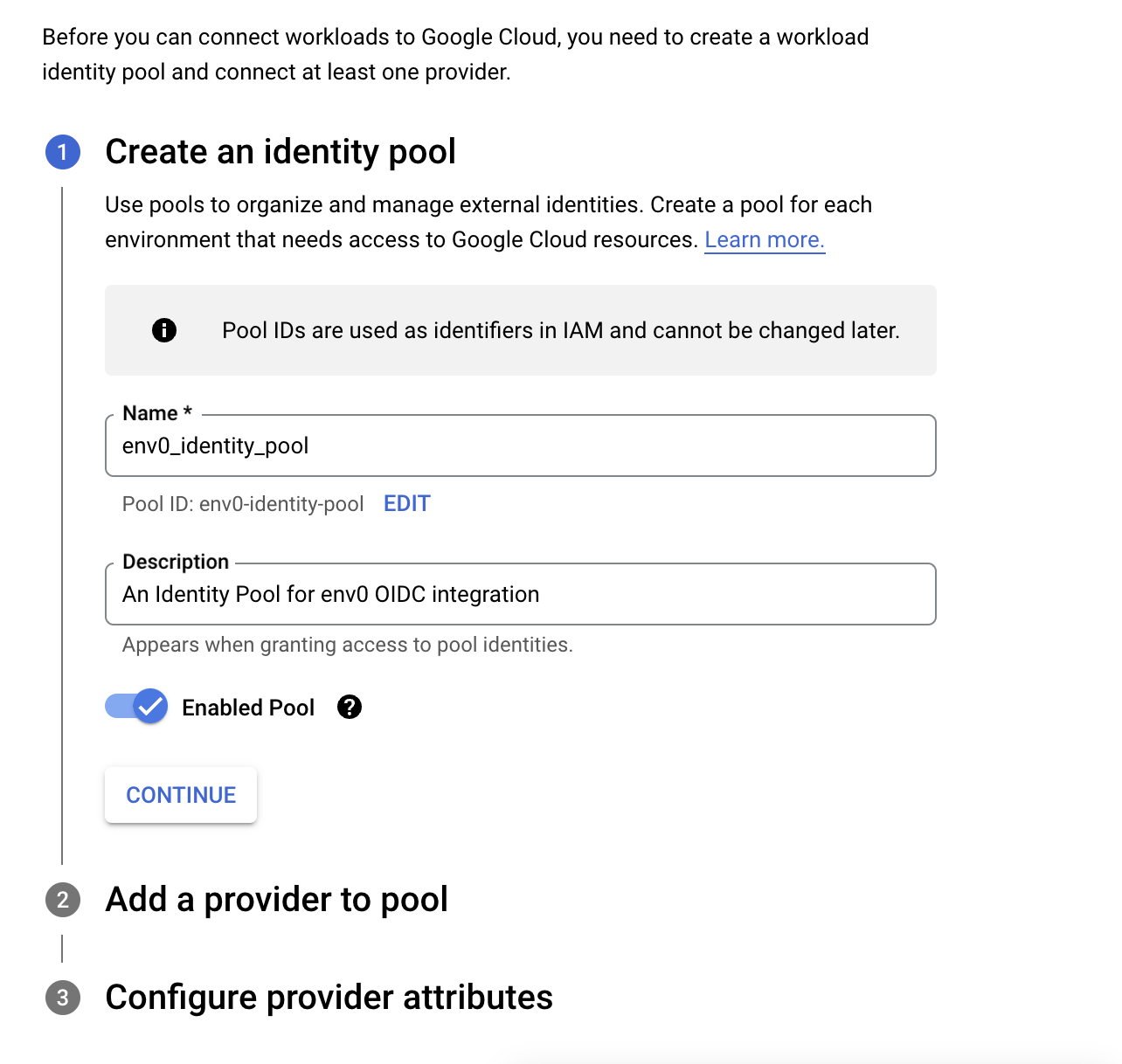
- In
Select a providerselection choose OIDC, add a Provider name, enter a Proivder ID - In the
Issuer (URL)section enterhttps://login.app.env0.com/ - In the
AudiencesSelectAllowed audiencesand enterhttps://prod.env0.comand click on the continue button.
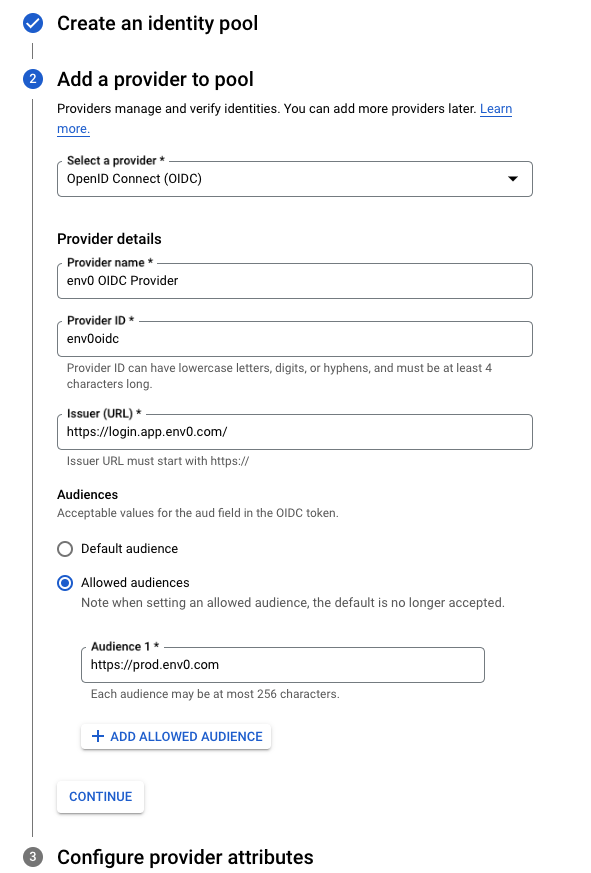
- In the
Configure provider attributesunder theOIDC 1enterassertion.sub - Click on the
Savebutton
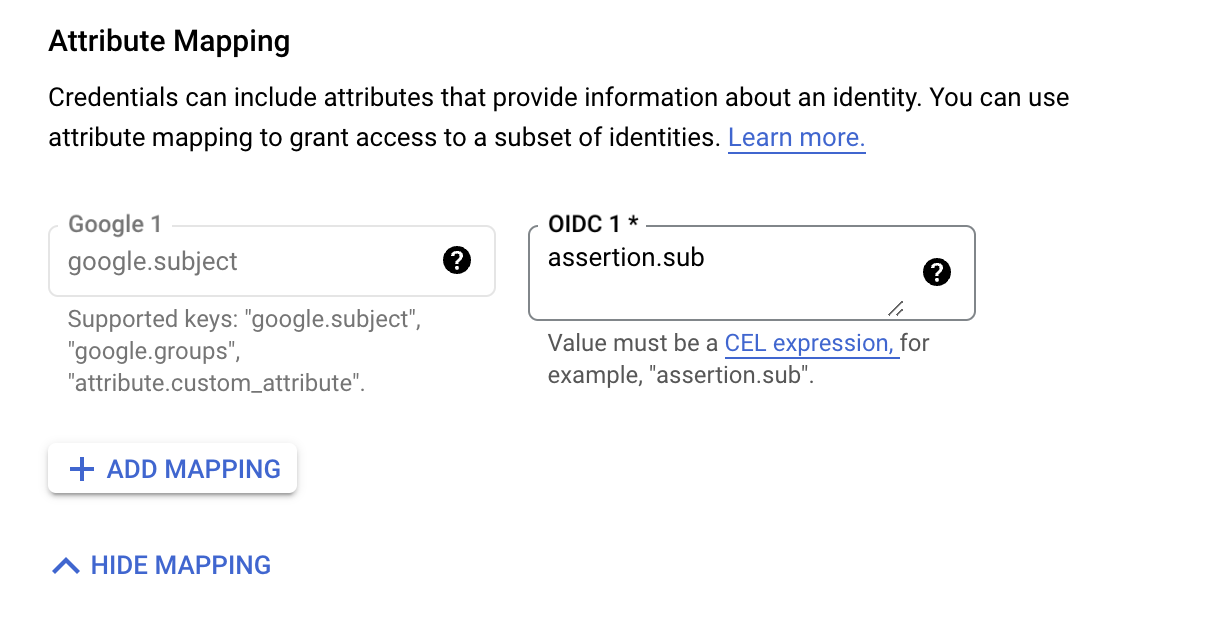
Adding Custom ClaimsIf you like to add more Custom Claims, for example, I would like to add the organization id claim I would click on the
Add Mapping button and add attribute.org_id in the Google text box, and in the OIDC I would add assertion.organizationId, and repeat step 14 with the organization id.Read more about Custom Claims here- Follow this guide to get you
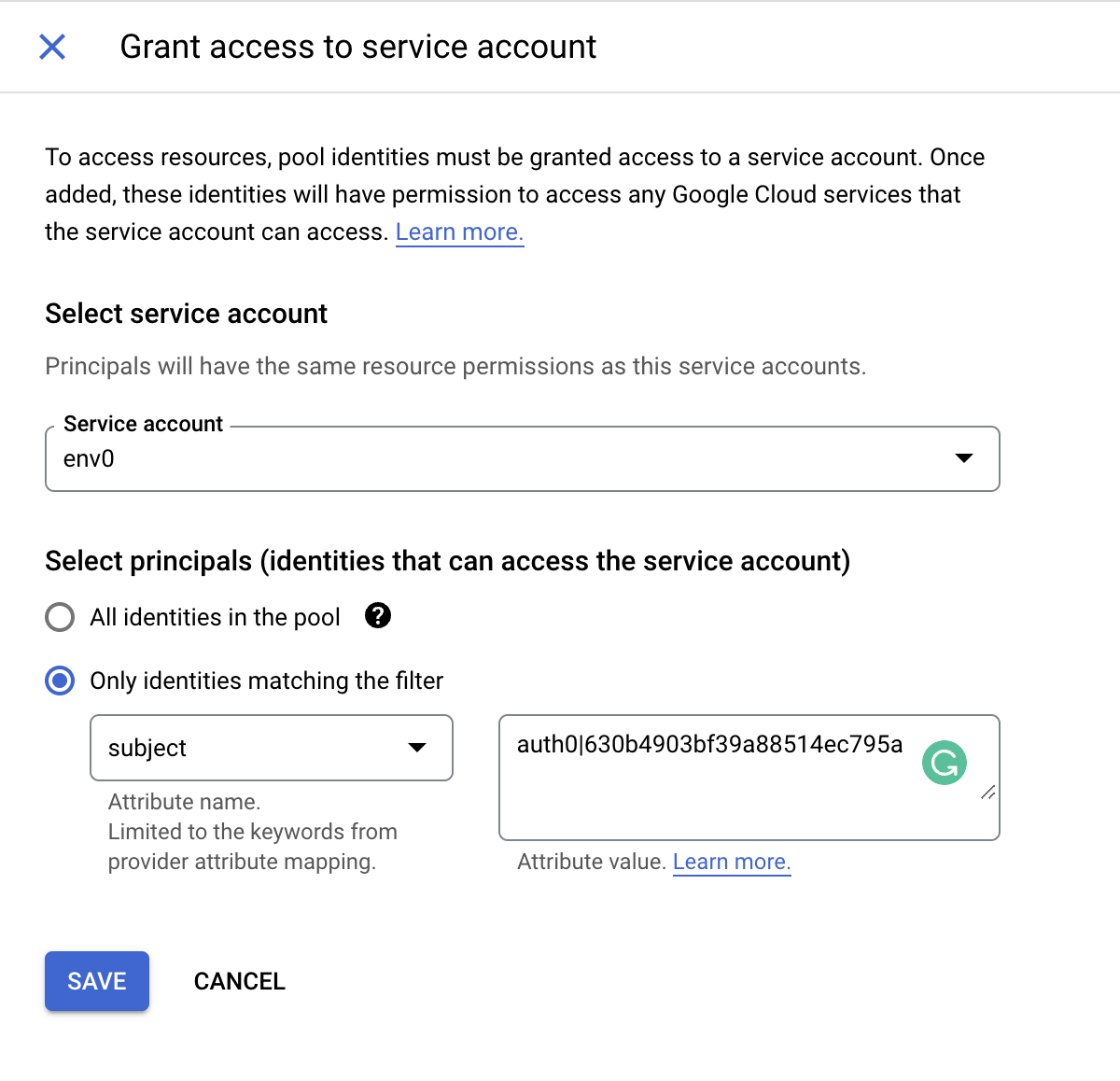
subvalue - In the Identity pool you’ve just created click on the
Grant Accessbutton - In the
Service accountselect the relevant service account you would like to associate the identity pool with. Make sure this service account has the relevant access to what your code needs in order to create those resources - Select the
Only identities matching the filterradio button and in theAttribute nameselectsubjectand in theAttribure valueenter the value of yoursubyou got from the previous steps, and click on theSavebutton
- In the
Configure your applicationmodal select the env zero provider you have created, insertenv0-oidc-token.txtas a filename inOIDC ID token pathtext box , and in theFormat typeselecttextand click on theDownload Configbutton - This will download a JSON configuration file that we will need during your deployment in env zero, and doesn’t contain any sensitive data on it:
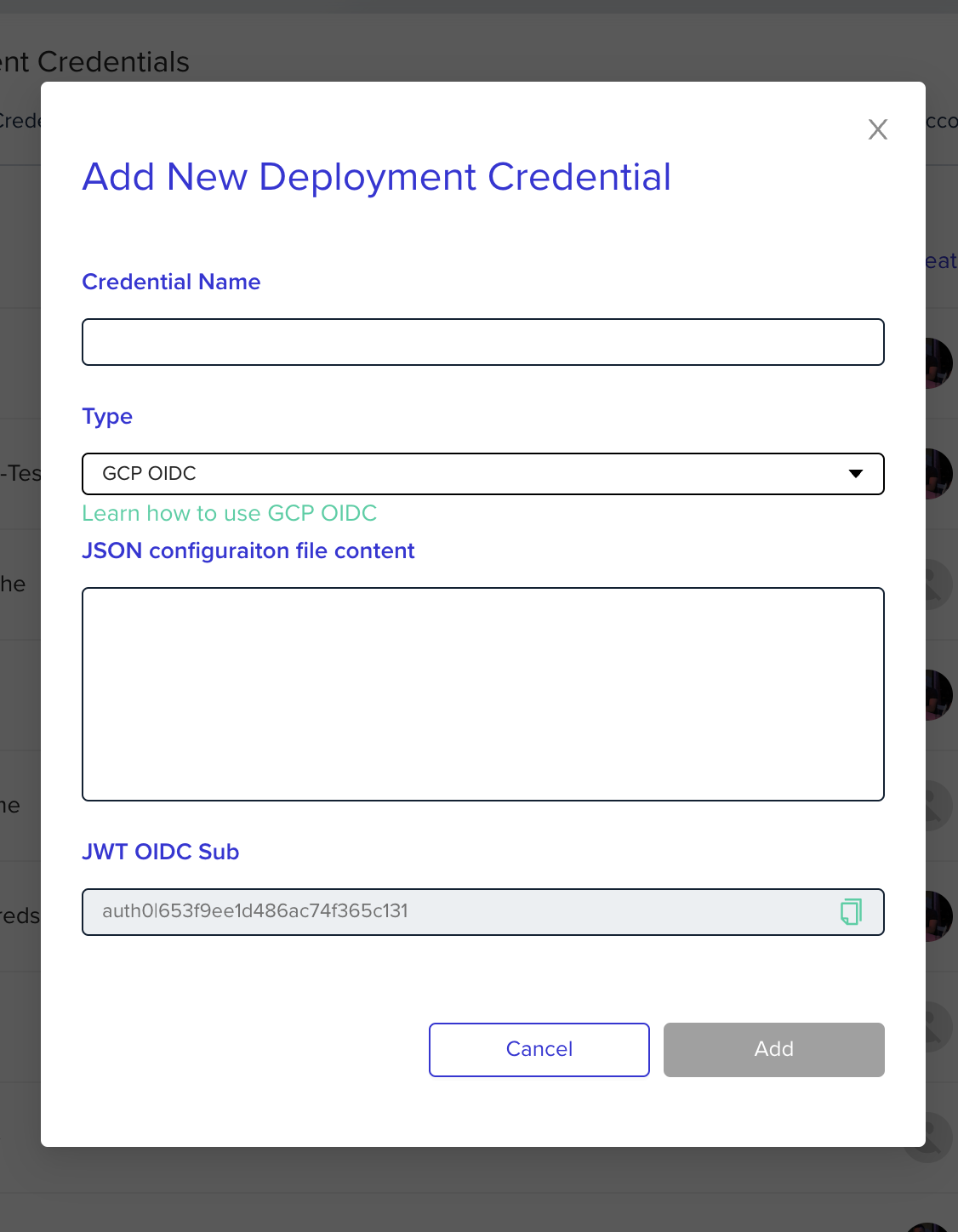
Configure env0 OIDC Credential
Go to the organization’s credentials page and create a new deployment credential. SelectGCP OIDC type and enter the following fields:
JSON configuration file content- The content of the JSON configuration file from the previous step
env0_credential_configuration.json in the deployment pod that will contain the configuration file content. To be able to use OIDC with GCP you will need to read that configuration file in your code. For example, using terraform, it will look like this:
Credential File PlacementThe file will be placed in the environment’s template path. The value is exposed by the ENV0_TEMPLATE_PATH variable.If no specific template path is set, the file will be placed in the directory defined by the variable: ENV0_ROOT_DIR.