Beta Feature - SCIM Provisioning is currently in beta. We’re actively improving the feature and welcome your feedback.
Overview
SCIM (System for Cross-domain Identity Management) enables your identity provider to automatically provision and deprovision users in env zero. Instead of relying on login-time syncing, SCIM keeps your user directory in sync continuously, so access is granted or revoked as soon as changes happen in your IdP.Prerequisites
- SSO must be configured - SCIM provisioning is only available after you set up an SSO connection (SAML or Azure AD)
- Edit Organization Settings permission is required
Setting Up SCIM
Navigate to SSO Settings
Go to Organization Settings > SSO. Below your SSO connection, you’ll see the SCIM Provisioning section.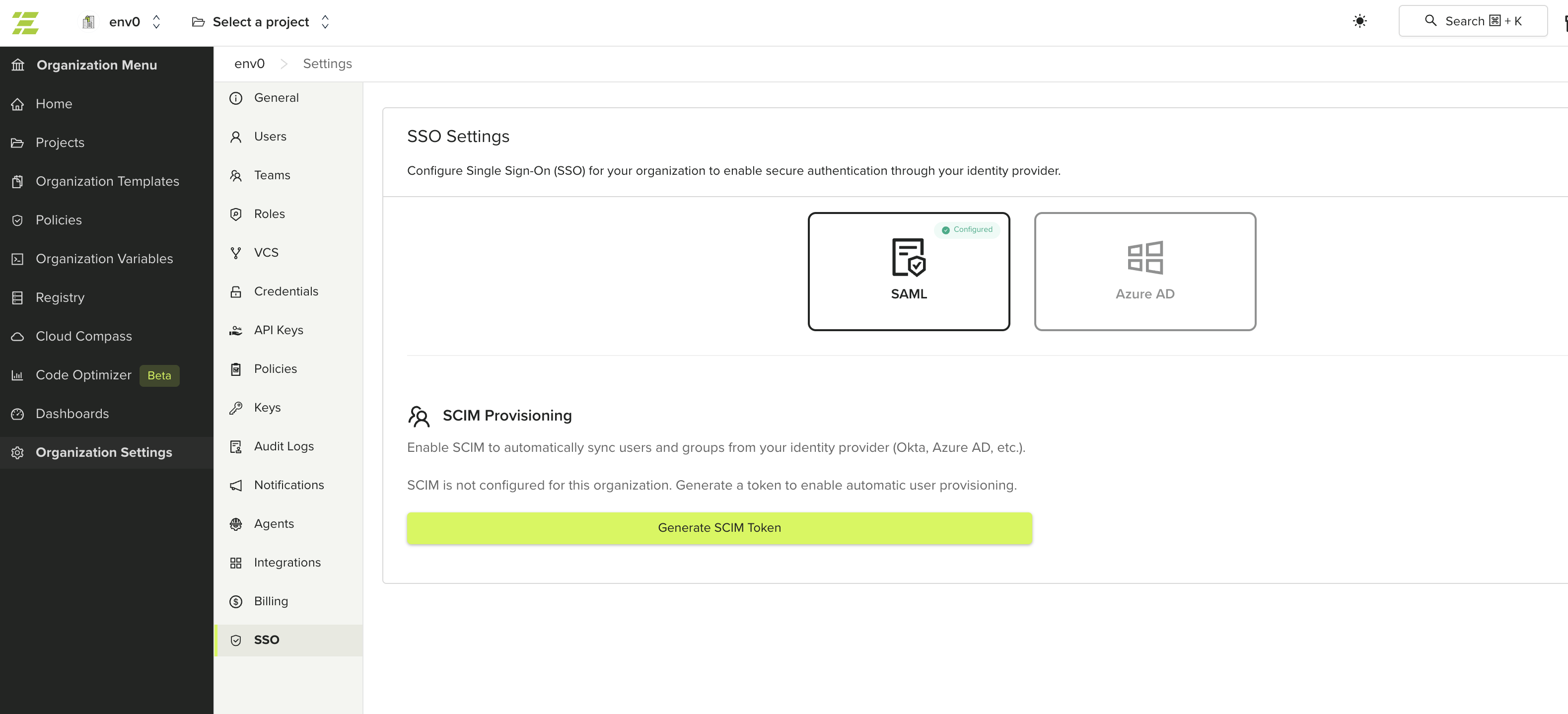

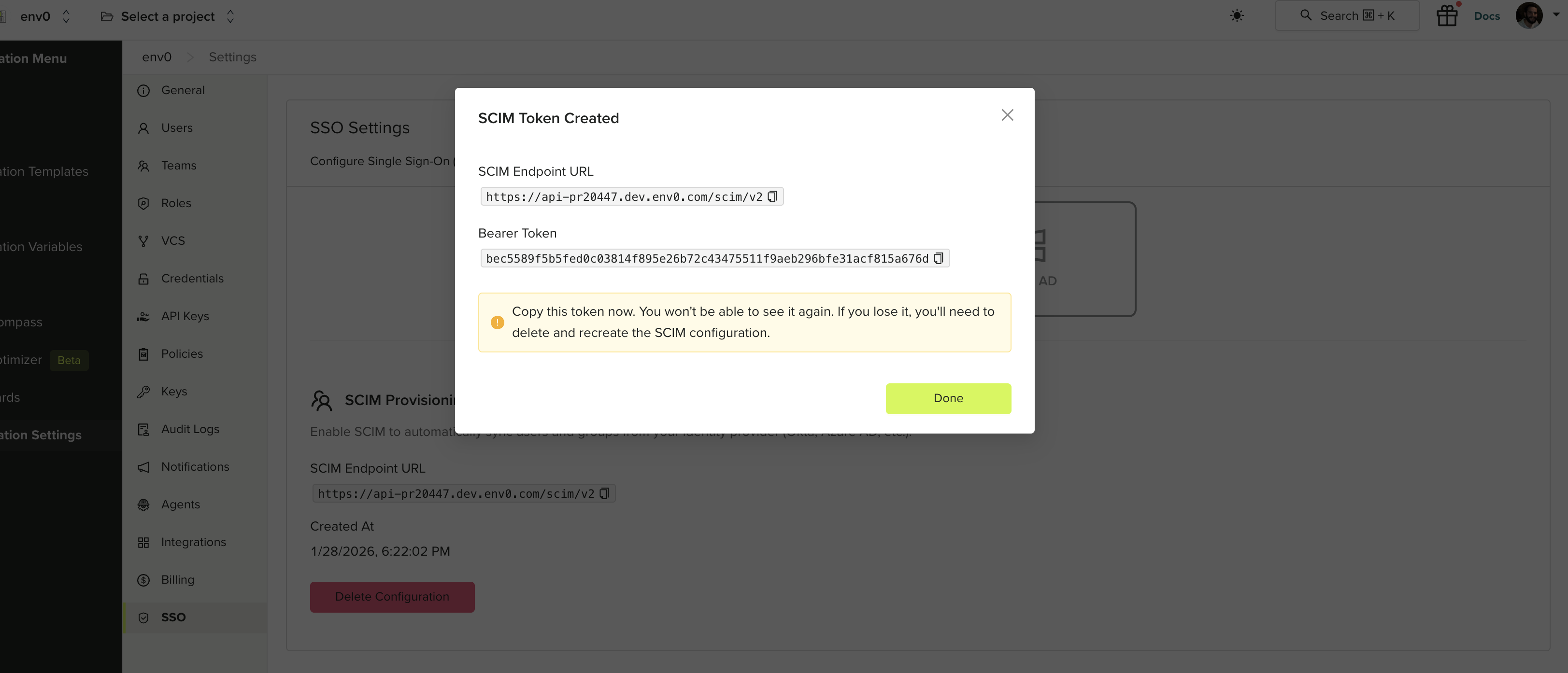
Generate a SCIM Token
Click Generate SCIM Token. This creates a bearer token and SCIM endpoint URL for your organization.
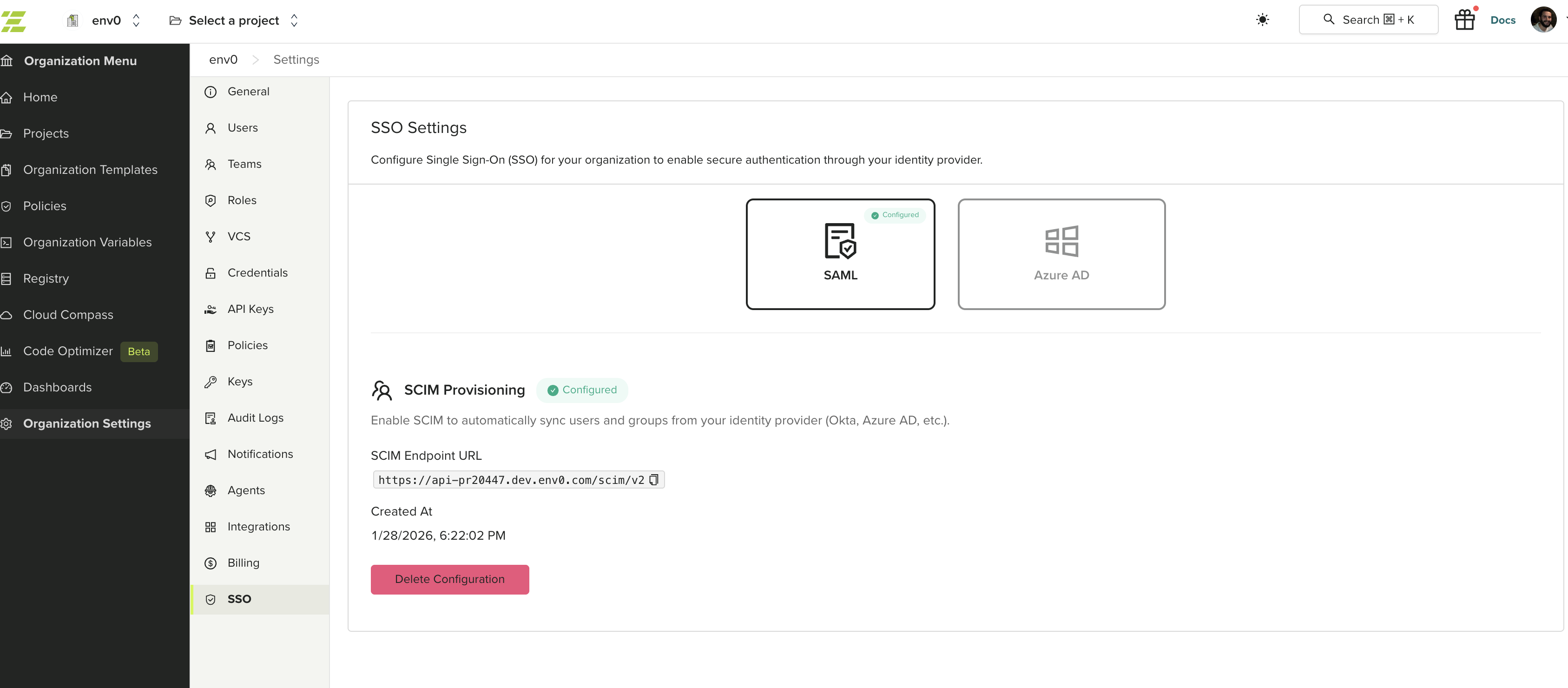
Configuring Your Identity Provider
Use the SCIM Endpoint URL and Bearer Token to configure provisioning in your identity provider. See your IdP’s documentation for SCIM setup instructions:- Okta - Configure SCIM provisioning in Okta
- Microsoft Entra ID (Azure AD) - Configure SCIM provisioning in Entra ID