Commenting with env zero commands on a pull request makes it possible to interact with your env zero environments without having to log in to the env zero platform.
For an env zero environment to be actionable in a pull request comment, the following prerequisites must be met:
- The environment needs to have originated from a VCS-integrated template, and its configured revision must be the same as the base branch (target) of the pull request
- The environment has ‘Enable PR Comments Commands for this Environment’ enabled
- (Optional) The environment has Alias set
Configuration
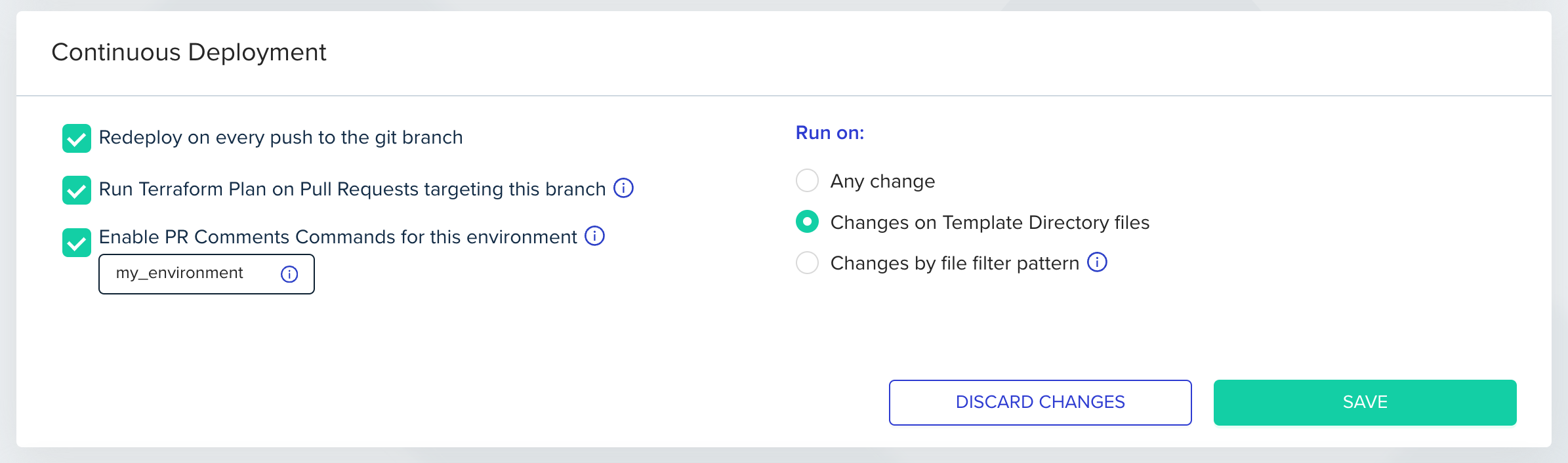
In order to configure this feature, you will have to enable the ‘Enable PR Comments Commands for this environment’ checkbox. Go to ‘Environments’, select ‘Settings’ and check ‘Enable PR Comments Commands for this environment’. Optional: Set an alias for each environment in which you would like to run individual commands using an-e flag. This alias will be used as a unique environment identifier when running a command from your VCS provider.Environment aliases may only contain letters, numbers, _, and -.
Even without setting an alias, the environment will still be included when using
--all or --path flags.
Self-hosted VCS provider supportTo enable this feature for GitHub Enterprise, Bitbucket Server and GitLab Enterprise, make sure your VCS Webhook is configured to send PR comments events.
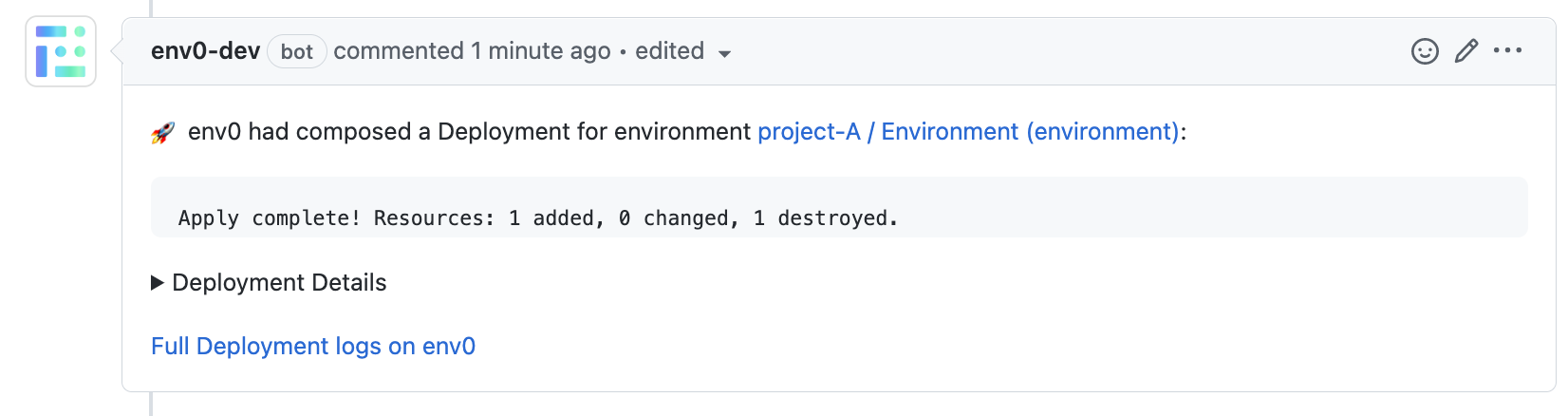
List of Affected Environments
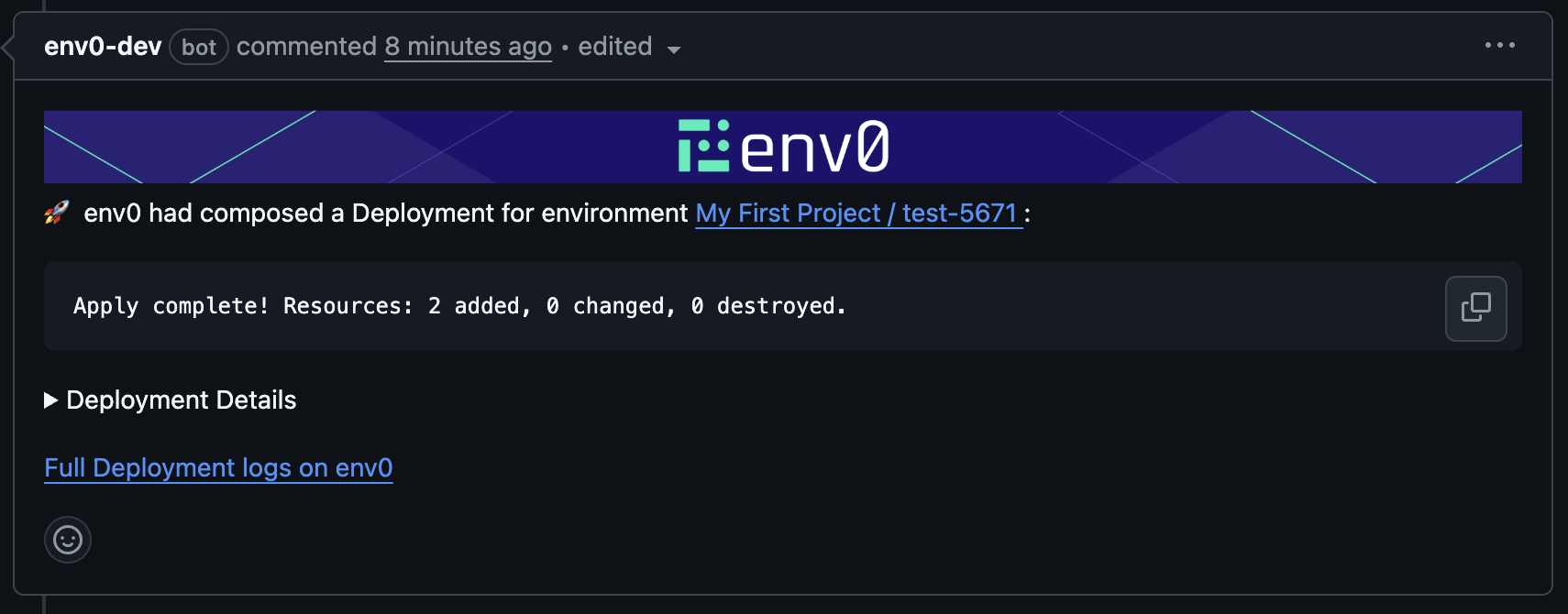
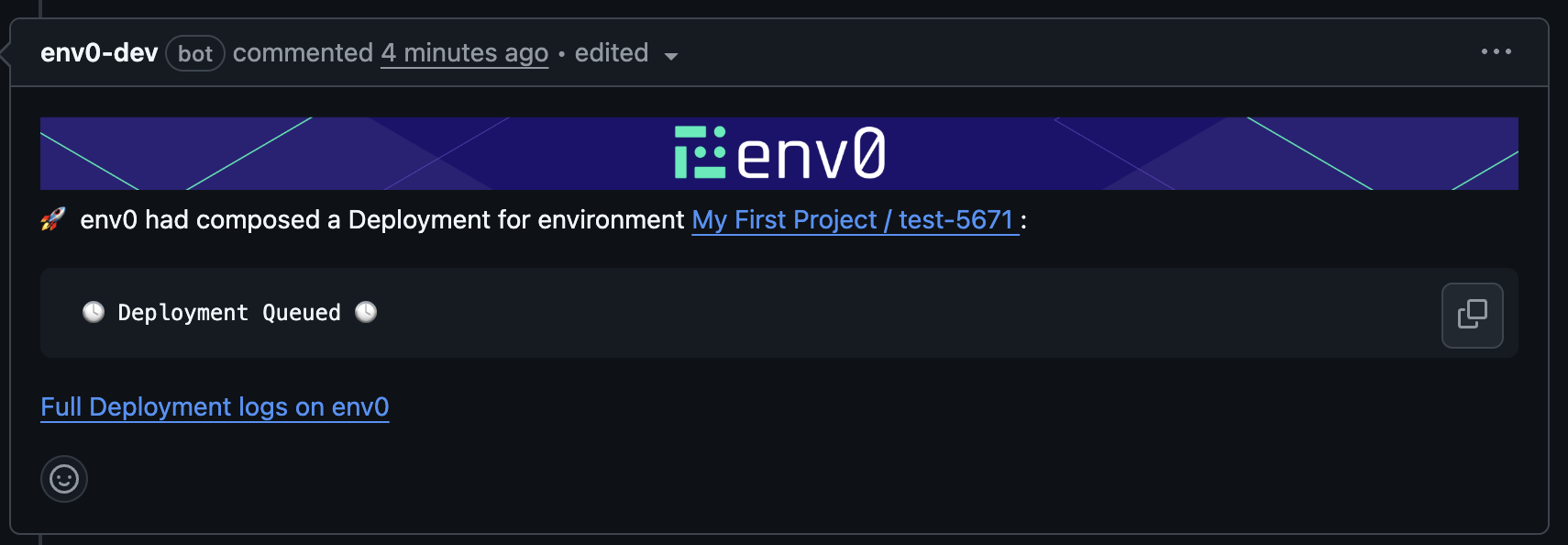
Every PR push will generate a PR comment, indicating which environments are affected by changes to this PR. An environment must enable the ‘Enable PR Comments Commands for this environment’ to be detected as affected, as described in the Configuration above. Below is an example of a comment which lists three affected environments and their full paths: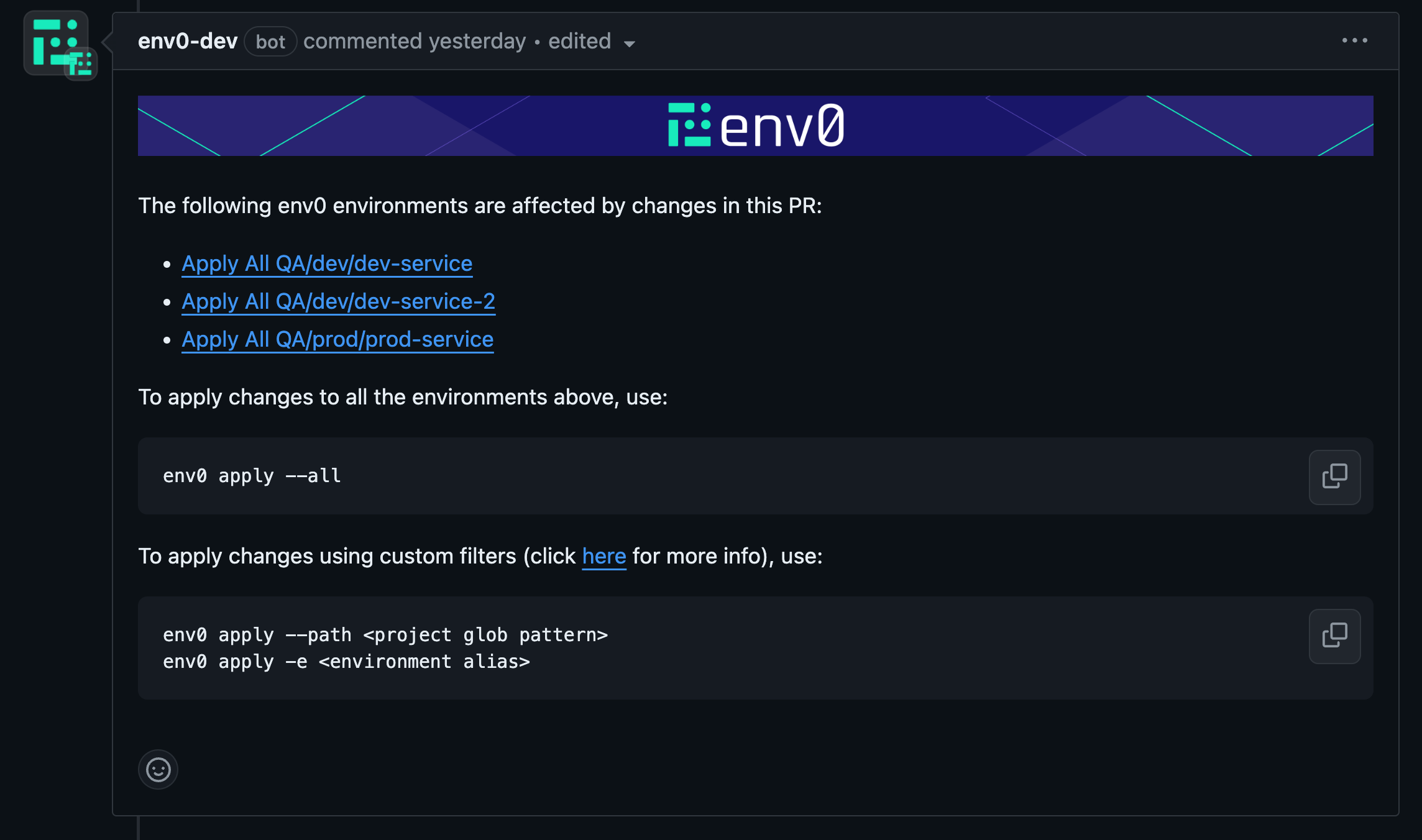
Supported env zero commands:
env0 help command
ℹ️env0 help - Lists all available commands.
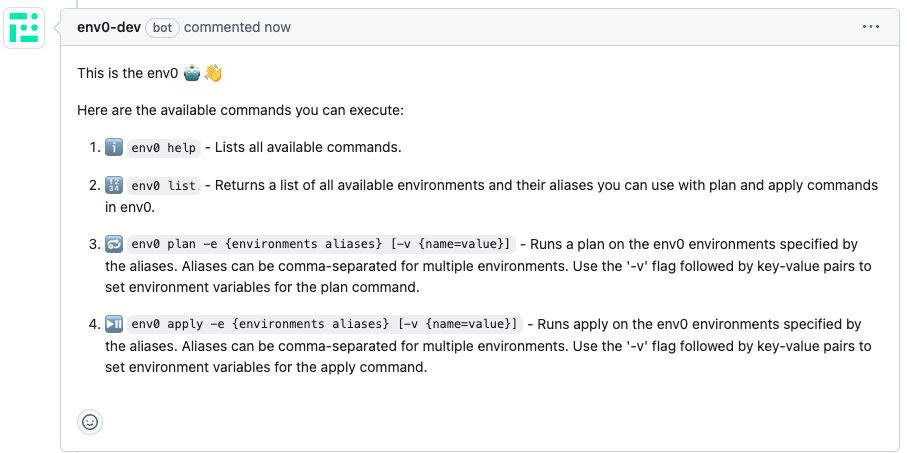
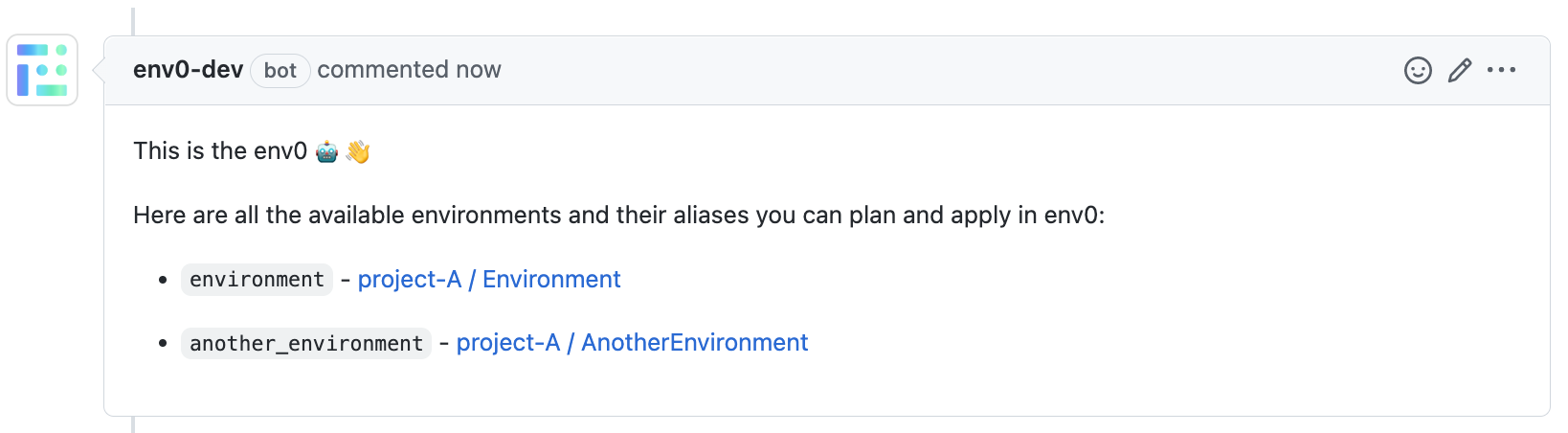
env0 list command
🔢env0 list - Returns a list of all available environments and their aliases to plan and apply in env zero.
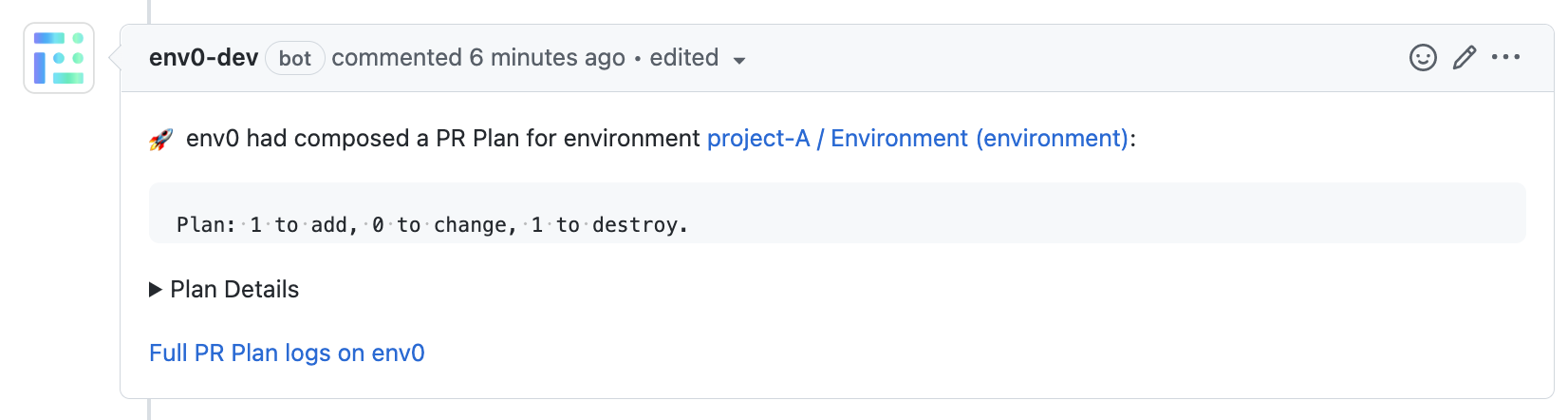
env0 plan command
🔂env0 plan --all [-v {name=value}] - Runs plan on all the affected environments listed in the affected environments comment above.
🔂 env0 plan --path "<path glob pattern>" [-v {name=value}] - Runs plan on all the environments listed in the affected environments comment above whose full path matches the given glob pattern path. Use quotes " around the glob pattern if it contains spaces.
🔂 env0 plan -e {environments aliases} [-v {name=value}] - Runs plan on a set of provided env zero environment aliases (comma-separated).
env0 apply command
⏯️env0 apply --all [-v {name=value}] - Runs apply on all the affected environments listed in the affected environments comment above.
⏯️ env0 apply --path "<path glob pattern>" [-v {name=value}] - Runs apply on all the environments listed in the affected environments comment above whose full path matches the given glob pattern path . Use quotes " around the glob pattern if it contains spaces.
⏯️ env0 apply -e {environments aliases} [-v {name=value}] - Runs apply on a set of provided env zero environment aliases (comma-separated).
Requires Approval Behavior in env zero ApplyBy default, applies triggered from PR comments are approved automatically.Why?
When using apply via PR comments, we assume that users rely on their existing VCS governance methods, such as:
- Status checks
- PR approvals
- Branch protection rules
Organization Settings → Policies page.Learn more about it hereSpecifying Environment Variables in plan and applyTo include multiple variables, use the following format:
Use Case: Terraform Environment Variables
This approach is especially useful for setting Terraform environment variables.For example, you can utilize theENV0_TERRAFORM_TARGET variable to perform Target Resources deployments, as explained in the Additional Controls:Apply Requirements
The apply command also verifies that the pull request has the following requirements:- GitHub - We won’t run the apply command if you have a protected branch in place and all the requirements are not met. You can read more about protected branches here.
- Bitbucket / Bitbucket Server - We verify that at least one person who isn’t the author of the PR approved the pull request, and that none of the participants requested changes. You can learn more about reviewing a pull request in Bitbucket and declining a pull request.
- Azure DevOps - We won’t run the apply command if you have required branch policies checks that failed.
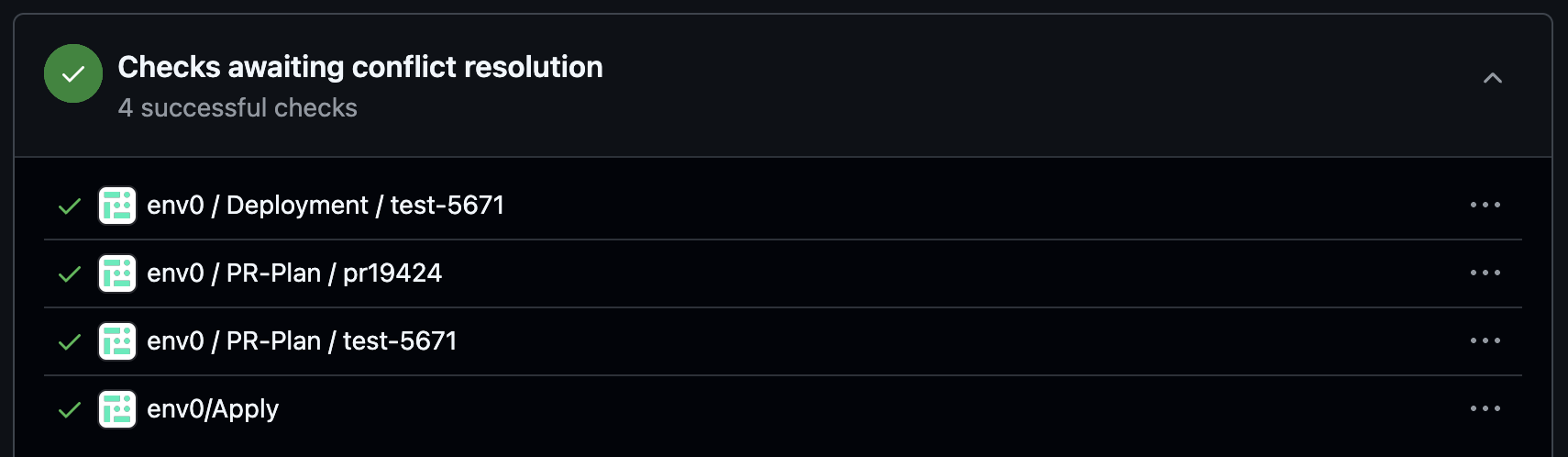
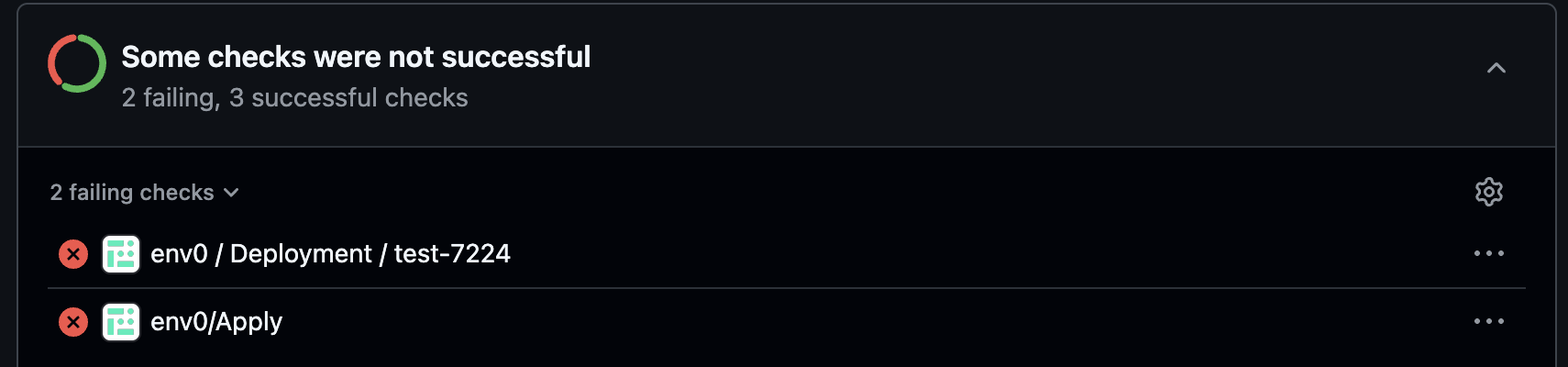
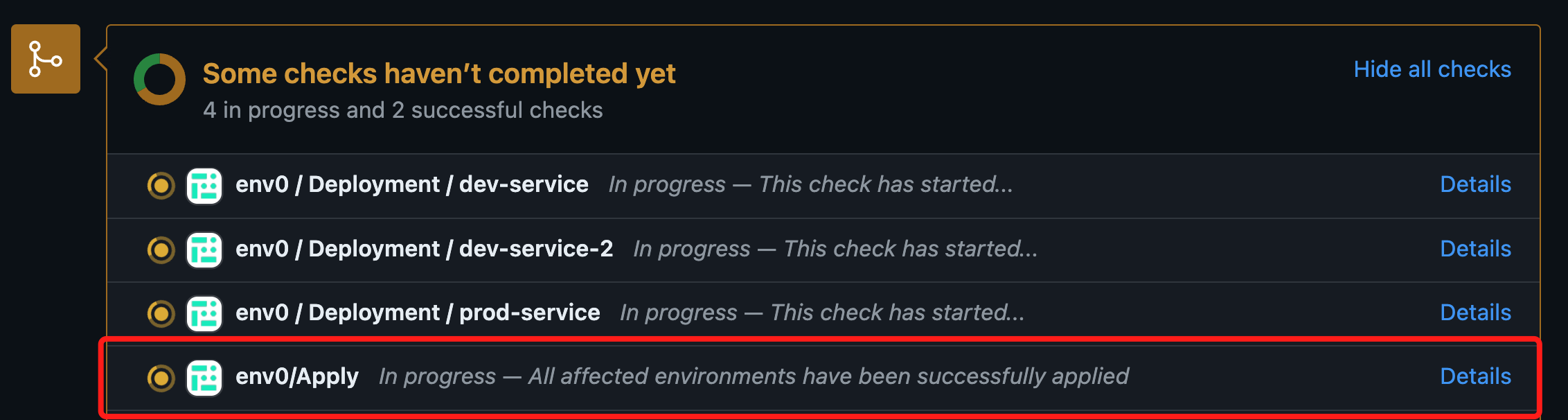
env0/Apply Commit Check
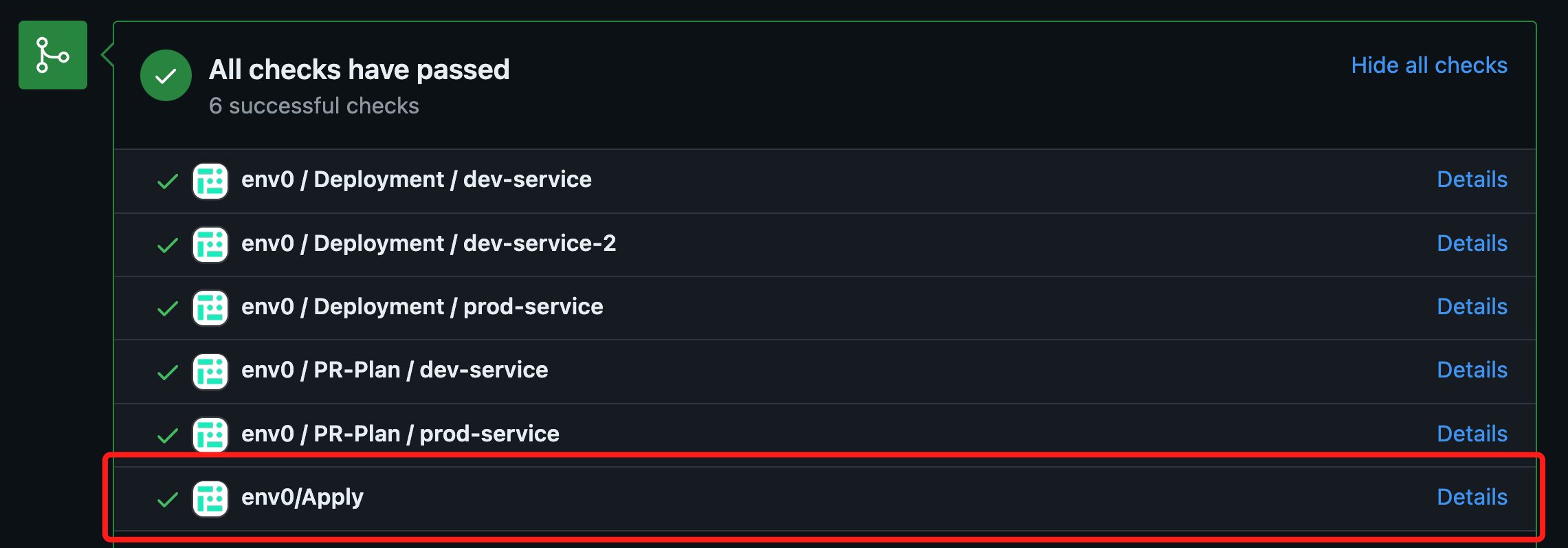
When runningenv0 apply --allor env0 apply --path <path>, a new env0/Apply commit check will be added on top of the individual deployment checks that you have per environment deployed:
success status once all the environments listed in the affected environments comment have been applied successfully. In case of failure in any of the deployments, the check’s status will be set to failure.
Enforce PR commenter permissions on env zero
With env zero, you can restrict your users’ permissions through role-based access controls. One drawback of using PR Comment Plan and Apply is that the VCS provider determines your users’ permissions. By default, anyone with comment permission on your repository can run a Plan or an Apply on your environments. Enforce PR commenter permissions on env zero is an organizational policy that lets you apply your env zero permissions to your VCS provider users. When turned on, env zero will validate that a user trying to run PR Comment Commands have adequate permissions.Turning on the policy for your organization
Navigate to ‘Organization Settings’ then go to ‘Policies’ and check ‘Enforce commenter permissions on env zero’.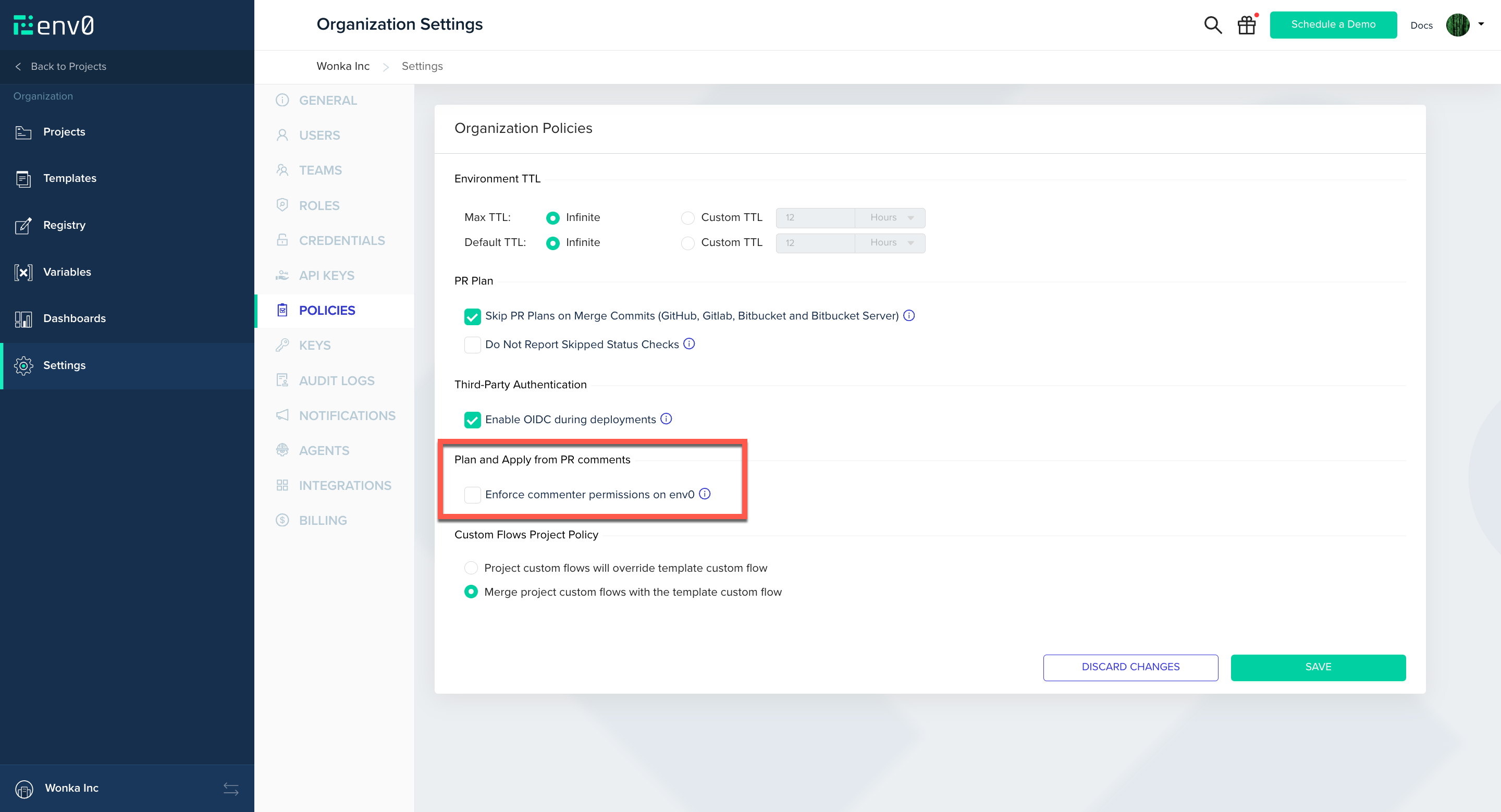
Map VCS provider user
Now that the feature is turned on, every user across the organization who wishes to use the PR comments flow must set up a mapping of their VCS provider user.First you will need to get your VCS provider user ID from one of the supported VCS providers.
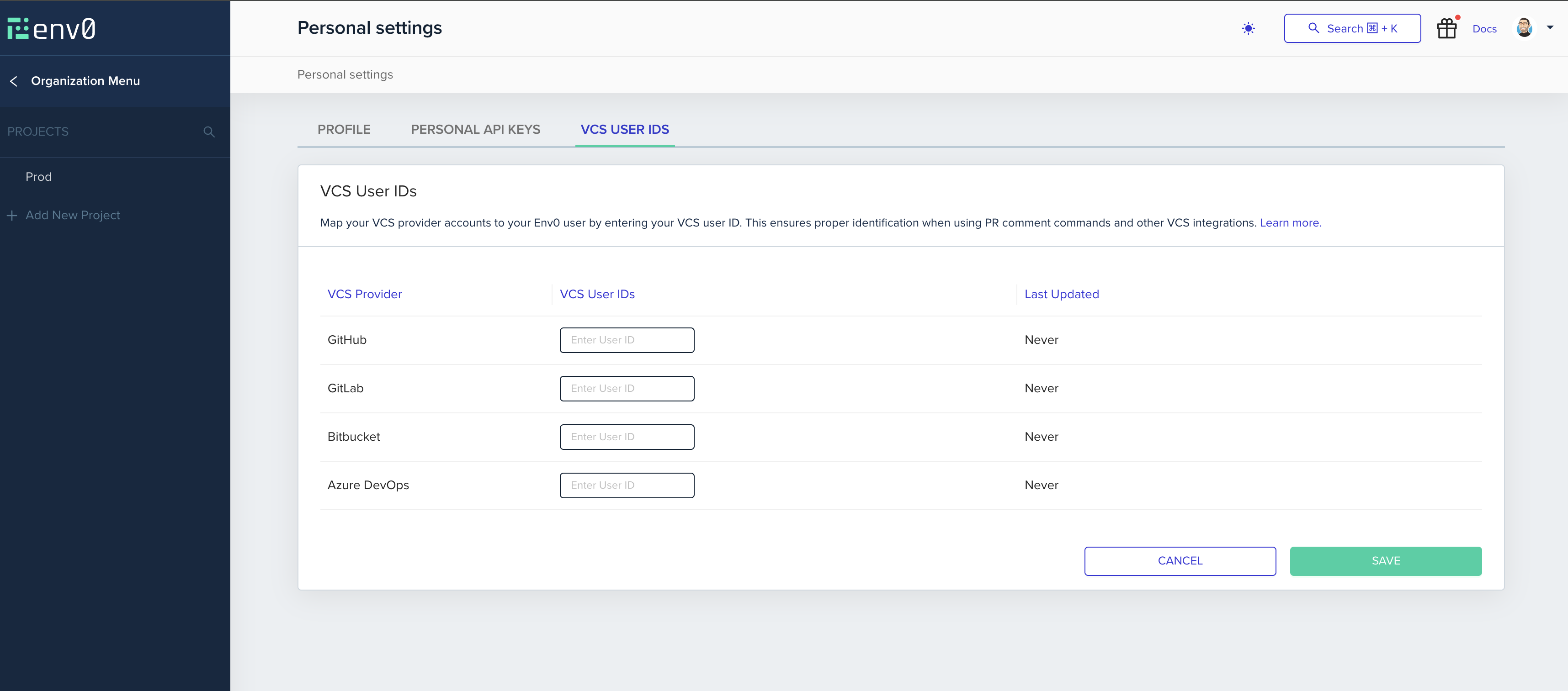
Setting your VCS user in env zero
Now that you have your VCS provider user ID, head over to your env zero account, click on the avatar image in the top right corner, and click on ‘Personal Settings’ to enter your profile page.In the VCS user ids tab, enter the ID from the previous step in the VSC Provider User ID textbox and click on the ‘Save’ button.
GitHub
While logged in to your GitHub account, click on your profile image in the right top corner of the page and copy your username.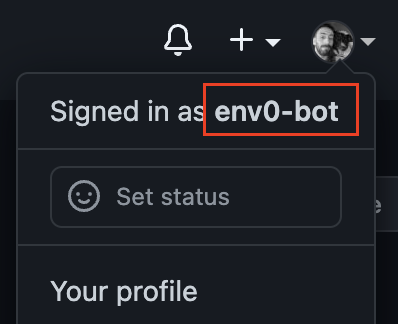
Bitbucket
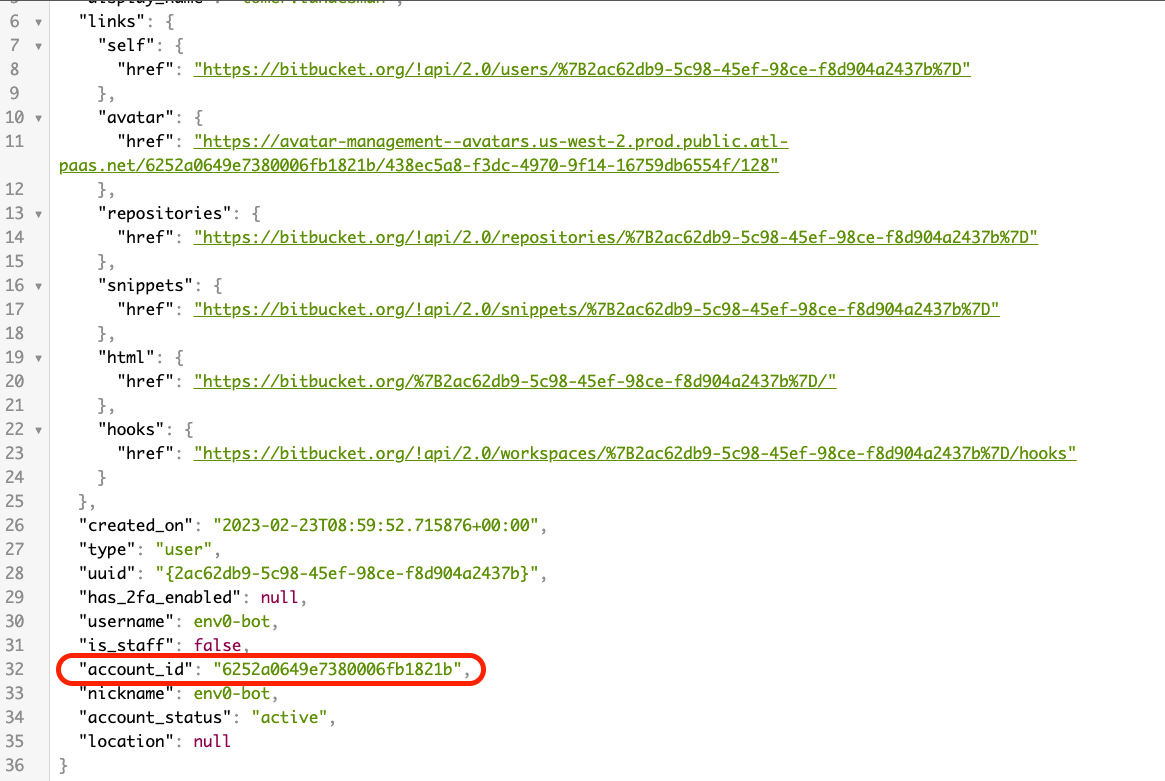
While logged in to your Bitbucket user, visit this URL from your browser. you will receive a JSON from which you will need to extract theaccound_id field.
Bitbucket Server
While logged into your Bitbucket Server account, go to your profile and locate the username by your avatar.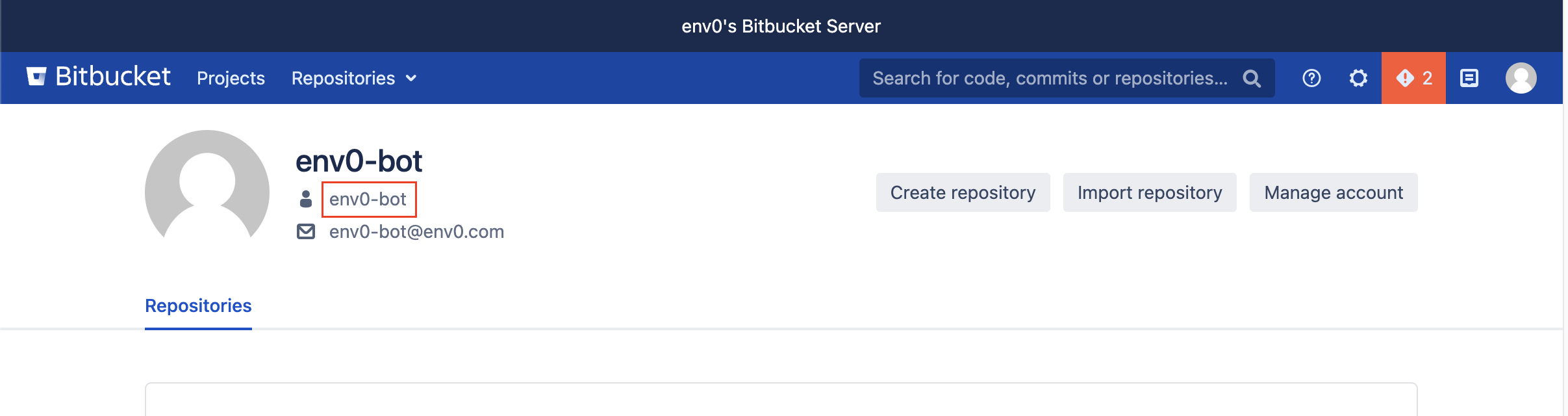
GitLab / GitLab Enterprise Edition
While logged into your GitLab account, navigate to the ‘Profile’ tab and ‘Edit Profile’ or “kebab” menu to find and copy your user ID.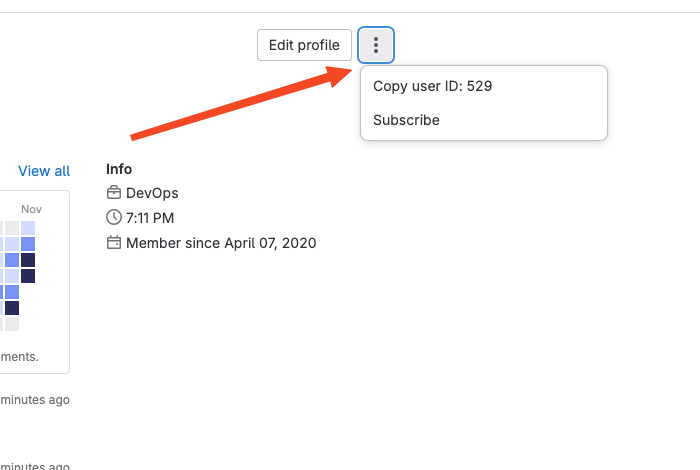
Azure DevOps
While logged in to your Azure DevOps account, click on your profile image in the right top corner of the page and copy your unique user ID.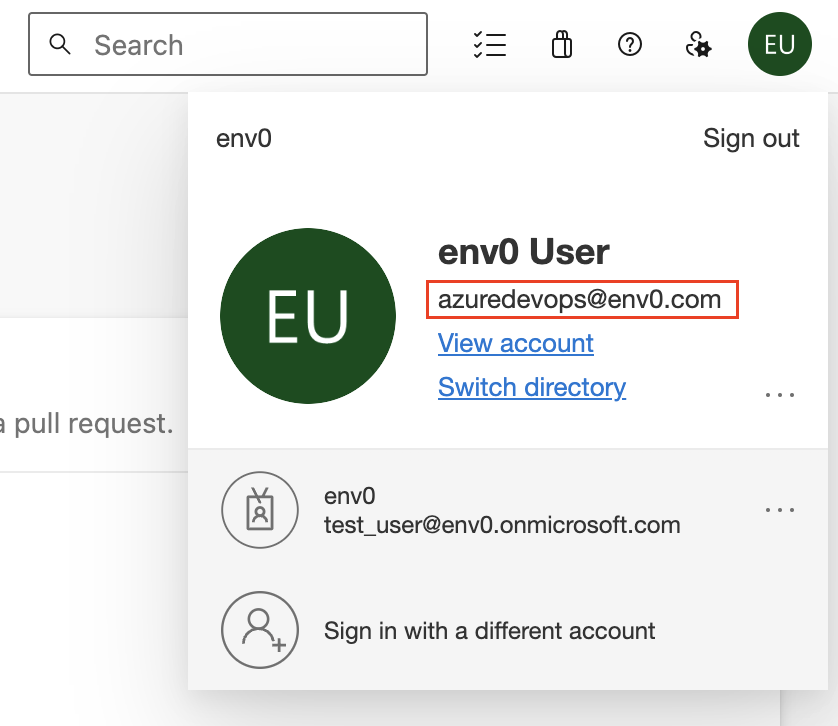
Additional Content
Status Checks for PR Comments
env zero offers the convenience of tracking the deployment status of your PRs directly from your Git provider’s interface. By integrating this feature into the familiar UI, you not only gain visibility into deployment statuses, but also leverage it to enhance your CI pipeline, using checks to enforce successful infrastructure deployments.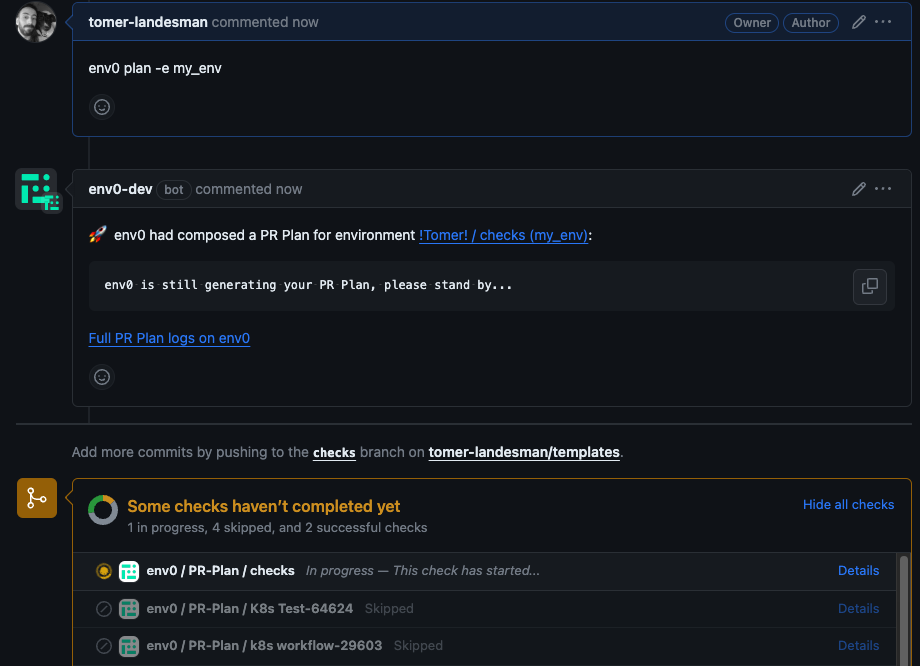
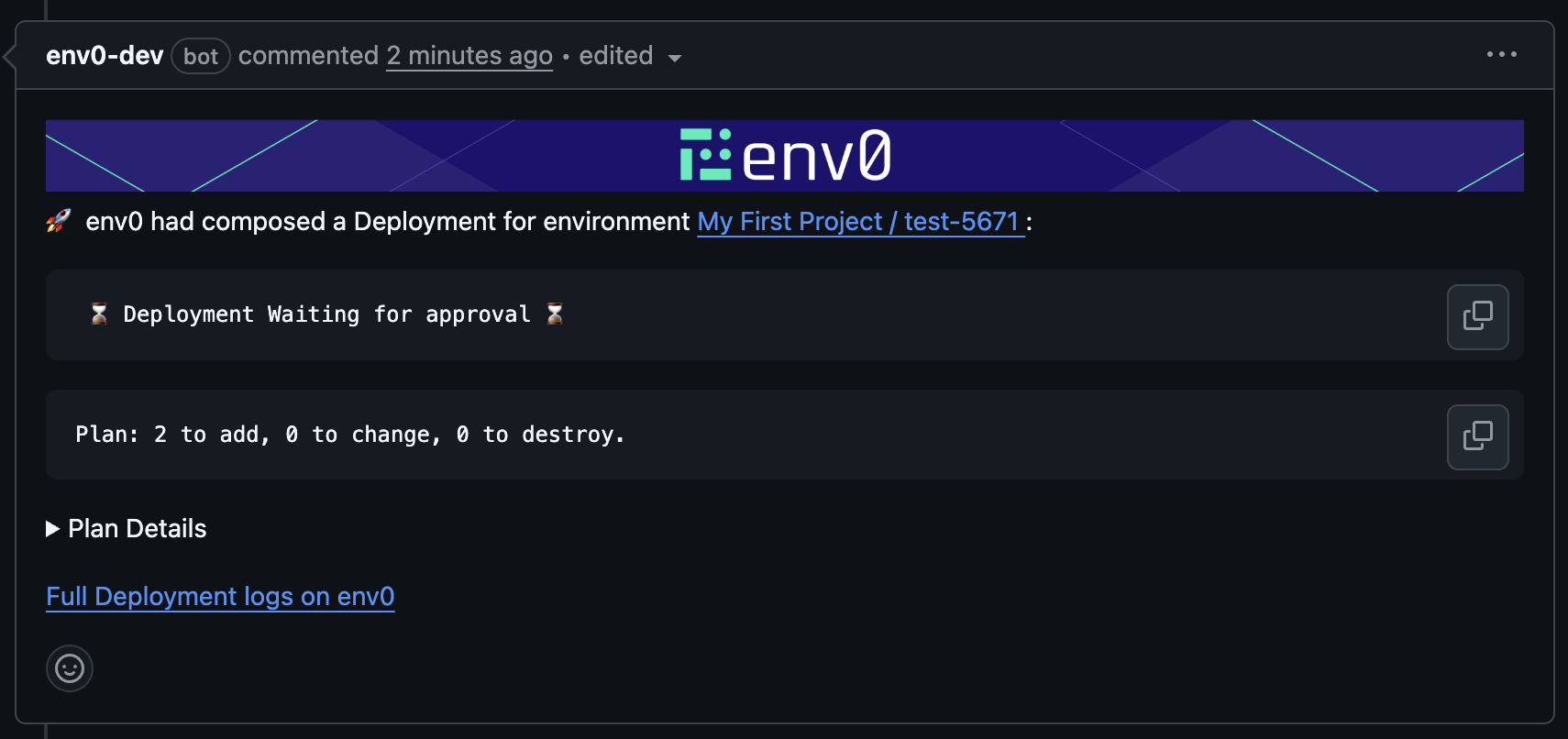
Require approval for PR comment applies
To require approval for applies triggered by PR comments, you must enable the “Require approval for PR comment applies” policy in Organization Settings → Policies. With this policy enabled, running env zero apply will trigger a deployment that will wait for manual approval.Once the plan step finishes, the plan results will be posted as a comment on the PR:
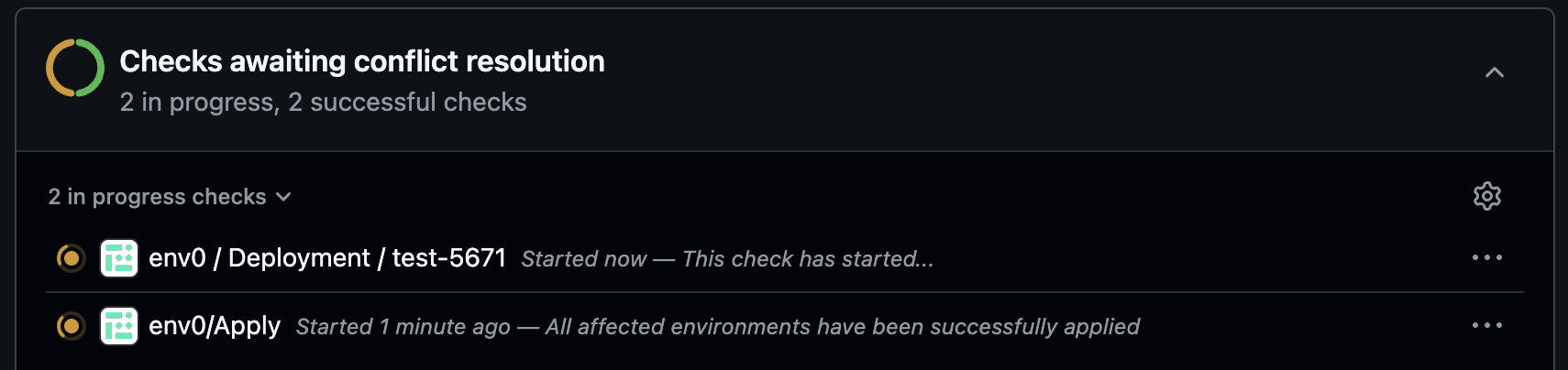
env0 approve command
🔂env0 approve --all [-v {name=value}] - Runs approve on all the affected environments listed in the affected environments comment above.
🔂 env0 approve --path "<path glob pattern>" [-v {name=value}] - Runs approve on all the environments listed in the affected environments comment above whose full path matches the given glob pattern path. Use quotes " around the glob pattern if it contains spaces.
🔂 env0 approve -e {environments aliases} [-v {name=value}] - Runs approve on a set of provided env zero environment aliases (comma-separated).
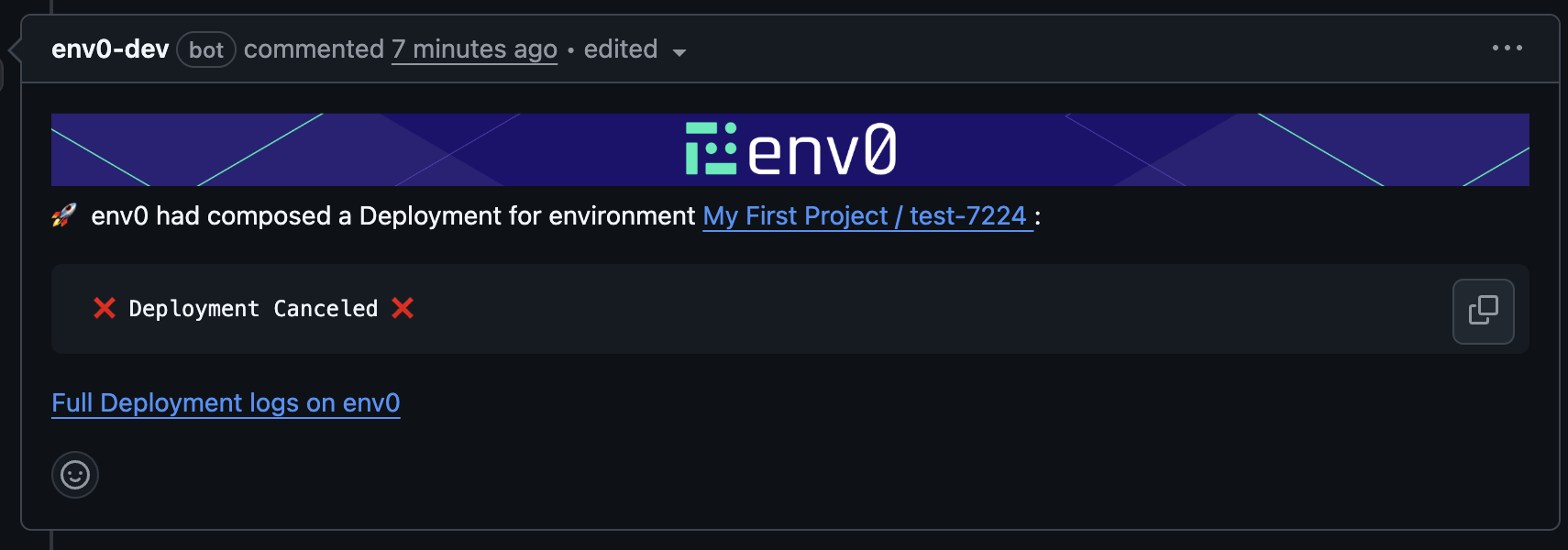
env0 cancel command
🔂env0 cancel --all [-v {name=value}] - Runs cancel on all the affected environments listed in the affected environments comment above.
🔂 env0 cancel --path "<path glob pattern>" [-v {name=value}] - Runs cancel on all the environments listed in the affected environments comment above whose full path matches the given glob pattern path. Use quotes " around the glob pattern if it contains spaces.
🔂 env0 cancel -e {environments aliases} [-v {name=value}] - Runs cancel on a set of provided env zero environment aliases (comma-separated).
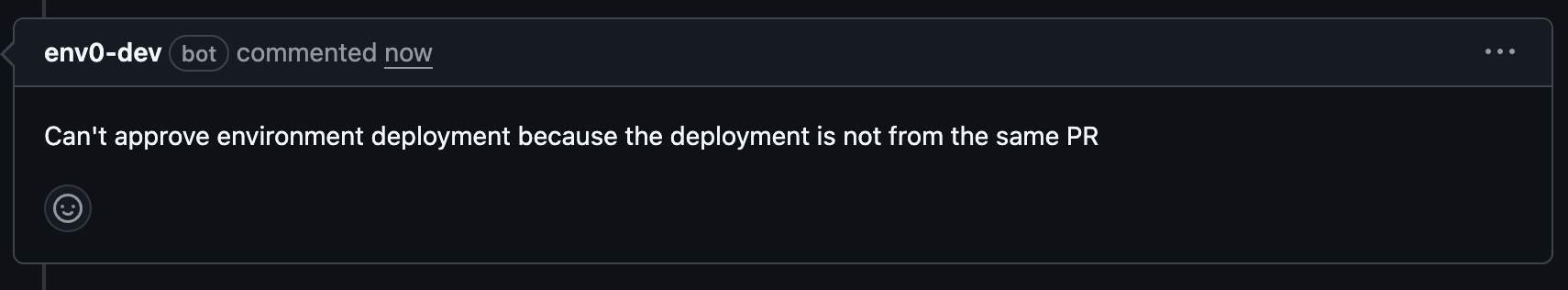
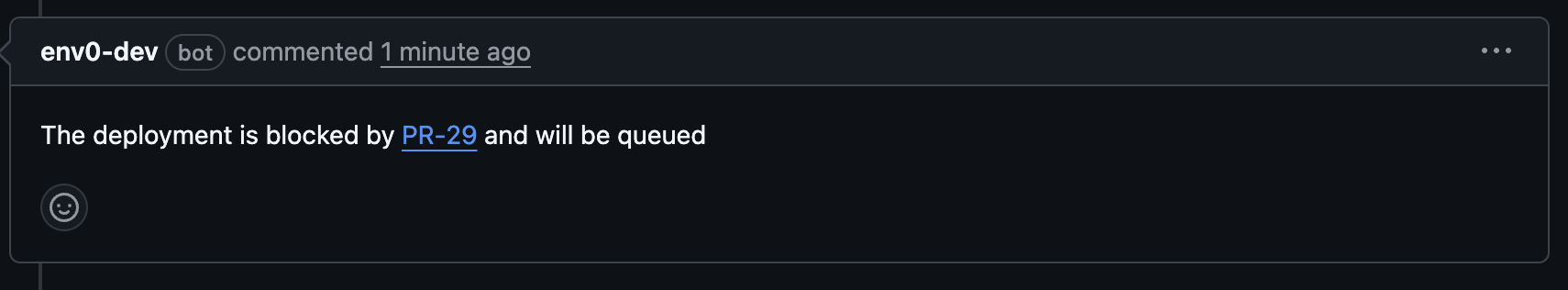
Both commands will only run for environments where the deployment awaiting approval was triggered from the same PR.
When approving, a deployment summary will be posted back to the PR, and commit checks will be marked as successful.