What are Environments?
Environments in env zero are your Infrastructure-as-Code (IaC) deployments - think of them as managed Terraform workspaces, CloudFormation stacks, Pulumi stacks, or Kubernetes namespaces. Each environment represents a complete deployment of your infrastructure code with its own state, variables, and lifecycle. Your users manage their environments in Projects where they can create, destroy, and redeploy environments. The user who creates an environment becomes the owner, while administrators manage access control and budgets through policies defined at the Project and Organization levels.Environment Mapping to IaC Tools
Here’s how env zero environments correlate with terms from various IaC and cloud management tools:- Terraform: An env zero environment is equivalent to a Terraform workspace or module
- Terragrunt: An env zero environment matches a specific Terragrunt configuration directory managing Terraform modules
- CloudFormation: An env zero environment corresponds to a CloudFormation stack
- Pulumi: An env zero environment maps to a Pulumi stack
- Kubernetes: An env zero environment relates to a Kubernetes namespace or a set of YAML files
- Helm: An env zero environment aligns with a Helm release
Creating Environments
Two Creation Approaches
You can create environments in two ways: Template-based Creation:- Use pre-configured templates for standardized, reusable deployments
- Built-in RBAC and governance controls
- Ideal for teams wanting consistency and standardization
- Connect directly to your Git repository for quick deployments
- Avoid template complexity for simple use cases
- Perfect for rapid prototyping and experimentation
Environment Lifecycle Management
Core Operations
Deploy: Runterraform apply (or equivalent) to create or update infrastructure
- Automatically runs
terraform planfirst to show changes - Stores outputs and state for future reference
- Sends email notifications on success or failure
terraform destroy (or equivalent)
- Can be triggered manually or automatically via TTL
- Queued if another operation is in progress
- For inactive environments: deploys from scratch with new TTL
- For active environments: updates with latest code changes
Environment States
Environments can be in one of these states:- Active - Successfully deployed and running
- Inactive - Successfully destroyed (manual or automatic)
- Deploy in progress - Currently being deployed
- Undeploy in progress - Currently being destroyed
- Failed - Errors encountered during deployment/undeployment
- Waiting for approval - Plan created, awaiting Deployer approval
Time-to-Live (TTL)
TTL controls automatic environment destruction:- Predefined values: 12 hours, 1 day, 3 days, 1 week, 1 month, infinite
- Custom dates: Set specific end-of-life dates
- Policy control: Admins can set defaults and maximums via TTL Policies
Advanced Operations
Continuous Deployment
Automatically redeploy environments on Git pushes to specific branches. See Continuous Deployment for setup.Bulk Operations
Manage multiple environments simultaneously - deploy, destroy, approve plans, lock/unlock, and more. Learn more in Bulk Operations.Workflow Triggers
Chain environment deployments for complex workflows (e.g., dev → staging → production). See Workflow Triggers.Plan on Pull Request
Preview infrastructure changes before merging code. Details in Plan on Pull Request.Access Control & Governance
Role-Based Permissions
Planner Role: Can create plans but requires Deployer approval for execution Deployer Role: Can execute plans and approve deployments Admin Role: Full control over all environment operationsApproval Workflows
- Manual Approval: Plans require Deployer review before execution
- Automatic Approval: Deployers and Admins can enable immediate execution
Environment Locking
Prevent changes to critical environments during maintenance. Learn more in Environment Locking.Key Features
Environment Management
- Resource tracking: View all cloud resources managed by each environment
- Deployment history: Complete log of all environment operations
- Import existing: Bring existing infrastructure under env zero management
- Archive/Unarchive: Manage environment lifecycle without destroying resources
Integration & Automation
- VCS Integration: GitHub, GitLab, Bitbucket, Azure DevOps
- Cloud Providers: AWS, Azure, GCP, and other platforms
- API Access: Programmatic environment management via REST API
- Terraform Provider: Manage env zero resources using Terraform itself
Environment Resources
When environments are active, you can view all managed resources organized by provider and type with search functionality.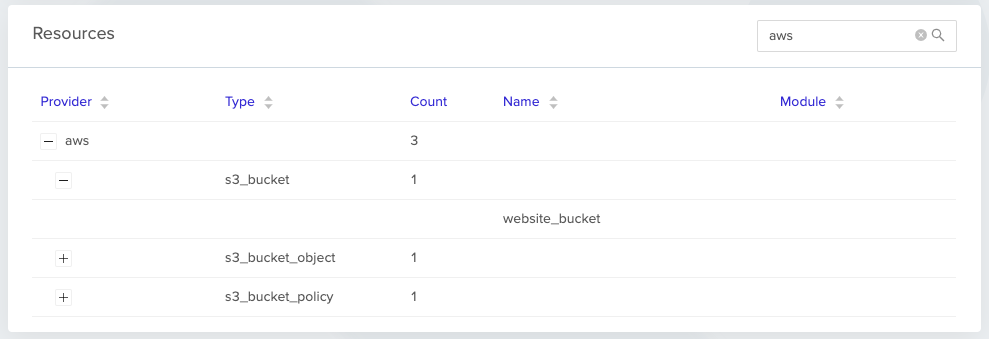
Best Practices
Development Workflows
- Use short TTLs for development environments
- Enable continuous deployment for dev branches
- Implement proper approval workflows for production
Production Management
- Set infinite TTL for production environments
- Require manual approval for all changes
- Use environment locking for critical systems