Introduction
This guide will detail the various steps required to integrate Microsoft Entra ID as an OAuth provider for your env zero organization. The current implementation will create an Microsoft Entra ID registered application with the Microsoft identity platform.This will be used for authentication only, where you define your users in your Microsoft Entra ID and enable them access to your env zero organization.
In addition, we also support group syncing of the logged in user to match those with env zero teams.
Steps
- Follow this guide to register an application in the Microsoft identity platform
- Leave the Redirect URI empty.
- In the platform setting you need to select
Web - Add a Redirect URI with this value:
https://login.app.env0.com/login/callback - Create a Client Secret.
- Upload the Application (client) ID and the Client Secret Value here.
(Optional) Provide either the email domain (env0.com) or the specific Microsoft tenant domain (e.g. env0.onmicrosoft.com) - Your env zero Organization ID can be found in your Organization > Settings tab.
Multitenant Microsoft Entra IDIf you are in a Multitenant environment, please check this setting:
Under “Authentication / Supported account types”
Select “Accounts in any organizational directory (Any Azure AD directory - Multitenant)”
Under “Authentication / Supported account types”
Select “Accounts in any organizational directory (Any Azure AD directory - Multitenant)”
Teams SyncingTeams will be synced each time a user will login with the following logic:
- env zero will create a new team if one doesn’t exists based on the group name we received from the OAuth provider.
- If the team exists in env zero we will not create a new team.
- We will assign the user to all the teams in env zero based on the group names he is part of in the OAuth provider.
- If the user was removed from a group in the OAuth provider we will remove him from the team in env zero.
Enabling Access
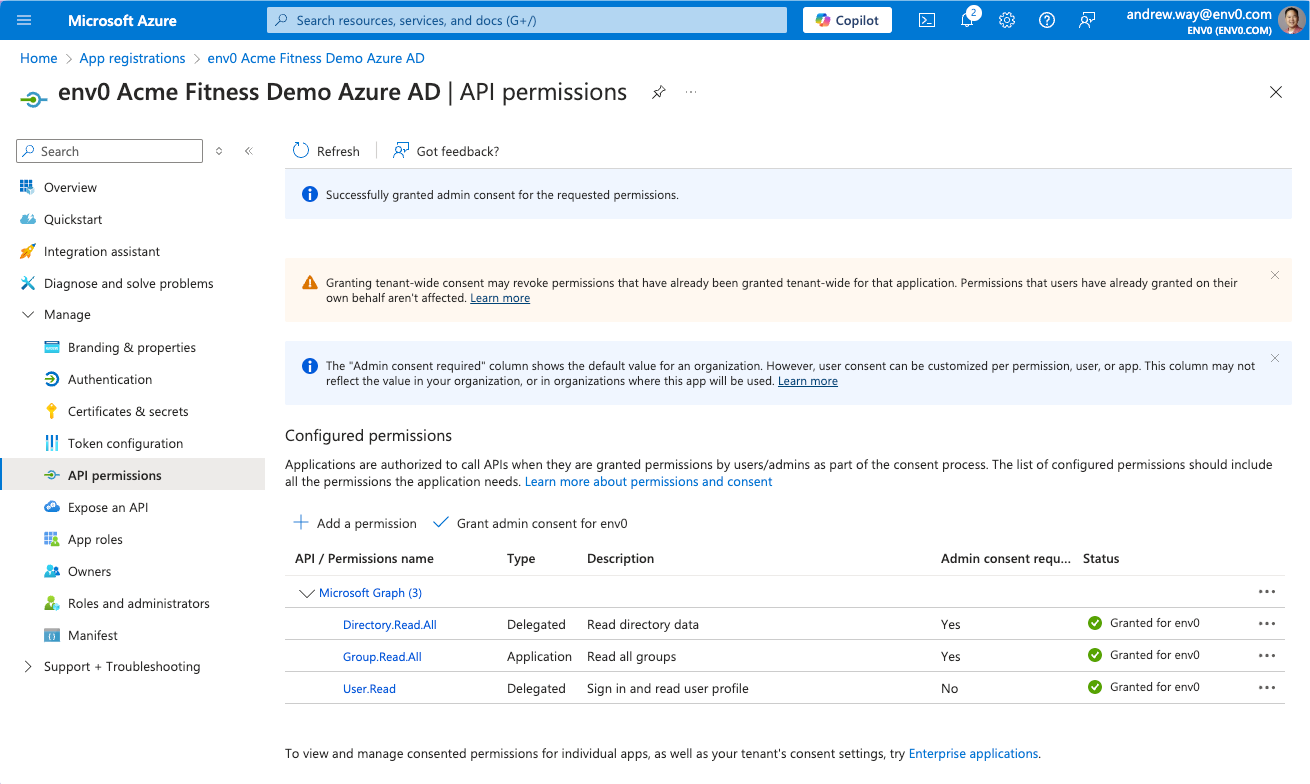
If your users are having trouble accessing the App Registration. Either under Manage > API Permissions or Security > Permissions, you will likely need to “Grant Admin consent for env zero” for **Microsoft Graph User.ReadSign in and read user profile**permissions, as well as Microsoft Graph Directory.Read.All permissions. See screenshot below for example.