Prerequisites
Before you begin, make sure you have:- Enabled OIDC in your env zero organization.
- Configured an Identity provider as explained in Set up an AWS OIDC authentication Guide.
Setup
To allow env zero to send logs to S3, you need an IAM policy with the necessary permissions. This policy will be attached to an IAM Role you use for OIDC authentication.The policy allows env zero to create and write to your S3 bucket.
Log Transporter Policy
Log Directory StructureLogs will be stored in your bucket with the following directory structure and file name format:
<bucketPath>/<logType>/<year>/<month>/<day>/<HH:mm:ss>_<5_random_chars>.log<bucketPath>: Your custom path (Optional)<logType>: Will be eitherenv0-deploymentsorenv0-auditsaccordingly
Self Configuration of CloudWatch Transporter
There are two ways to configure the integrations:-
In the env zero app
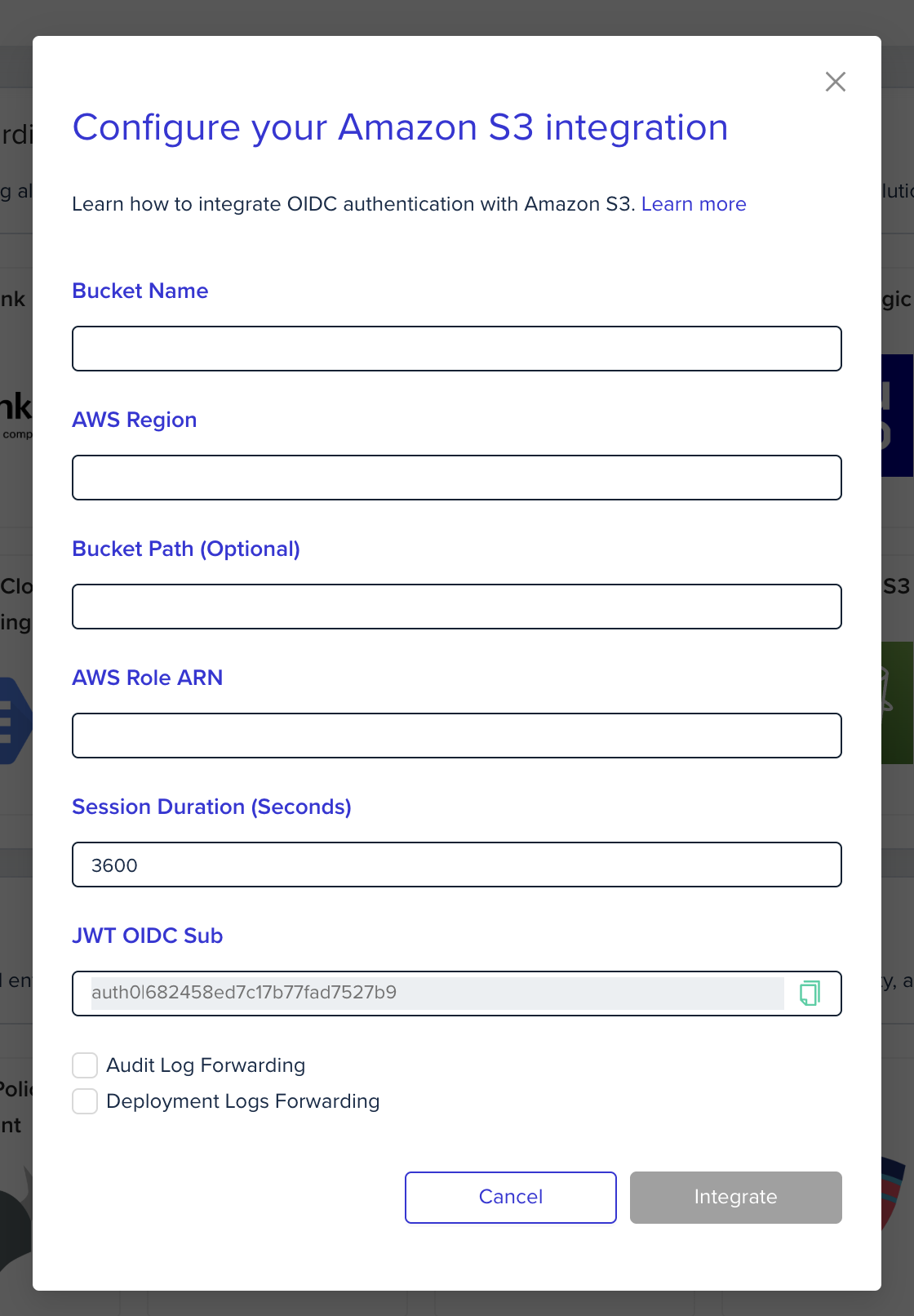
-
Using environment variables
In the env zero platform you will need to configure the following environment variables in any scope to forward the deployment logs. These are the relevant environment variables:Environment variable name Description Mandatory ENV0_S3_LOG_ROLE_ARNThe ARN of the IAM role associated with your OIDC provider. Yes ENV0_S3_LOG_BUCKET_NAMEThe name of the S3 bucket where logs will be stored. Yes ENV0_S3_LOG_AWS_REGIONThe AWS region where your S3 bucket is located. Yes ENV0_S3_LOG_BUCKET_PATHAn optional path (prefix) within the bucket to store the logs. No ENV0_S3_LOG_SESSION_DURATIONThe OIDC token session duration in seconds. Defaults to 3600 (1 hour) if not set. No
-
Audit Logs:
bucket path-env0-audits
-
Deployment Logs:
bucket path-env0-deployments